
In a virtual machine where I perform malware tests, I noticed that a conhost.exe process was constantly consuming around 50% of the CPU and allocating approximately 2.5 GB of space, even if it did not use the memory.

The main task of Conhost.exe is to provide the appearance and functionality of the command line window. This includes controlling the size, color and position of the window, displaying text and graphics, and processing user input.
However, the problem here is that it gets up again immediately after killing this process.

The reason why this process gets up again as you close it is that another process is actually doing this. So let’s try to look at the properties of this process to find its parent.

Next, let’s go to the TCP/IP tab to see if it has established a connection with any malicious IP or domain.

When we checked the IP and Domain, the IP address was flagged as malicious in one vendor;

We see that the reputation score of the domain is 98.9.

When we continue the examination, we can see that the parent process of conhost.exe is not visible, but its process id is included. When we check the parent’s process id, it is not included in process explorer either.

You can use procmon to understand which process is running conhost.exe. What we need to do is to start Procmon and stop procmon again after killing conhost.exe.
After stopping the Procmon log, let’s go to the filter section and add the process id of the new conhost.exe to the filter.

After adding the filter, we can see some of the activities of the new conhost.exe process from the moment it starts.

After double-clicking on conhost.exe again, we see that the ID of the parent process is 1592. When we enter ID 1592 as the PID filter in Procmon, we can see the process that starts conhost.exe.

To find out where the process is located, let’s double-click on the process and look at its properties.

When we go to the relevant path and ask virustotal for the hash of the file, we see that the file has been flagged as malicious by 47 manufacturers.


Then, when we delete the relevant file and look at the process explorer, we see that conhost.exe has risen again.

Then, when we look at the malicious file we deleted, we see that it has been recreated.

Then we changed our filter to see which process created the malicious file.
When we capture Procmon again, we see that another conhost.exe process created the malicious file.
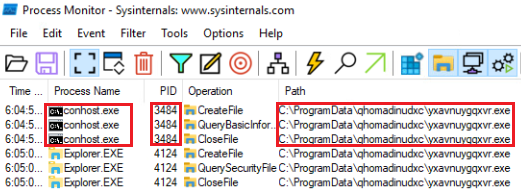
When we killed the conhost.exe process with ID 3484, we saw that the relevant malicious file was not created again and therefore conhost.exe, which consumes system resources, was not created again.

Leave a Reply