Good day everyone, today’s article is about comparing two well-known sandbox sites: Hybrid-Analysis and Cuckoo.
Since these two sandbox sites are professional sandbox sites that provide very accurate results, let’s see the detection rates with a real malware.
The malware I plan to use is a RAT malware. Let’s examine the results.
The first sandbox we will check is Cuckoo
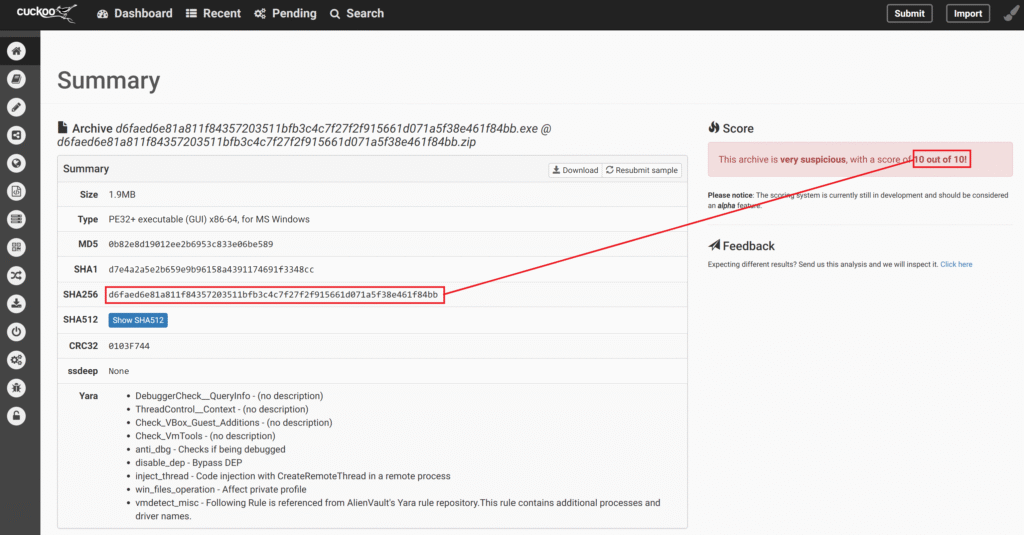
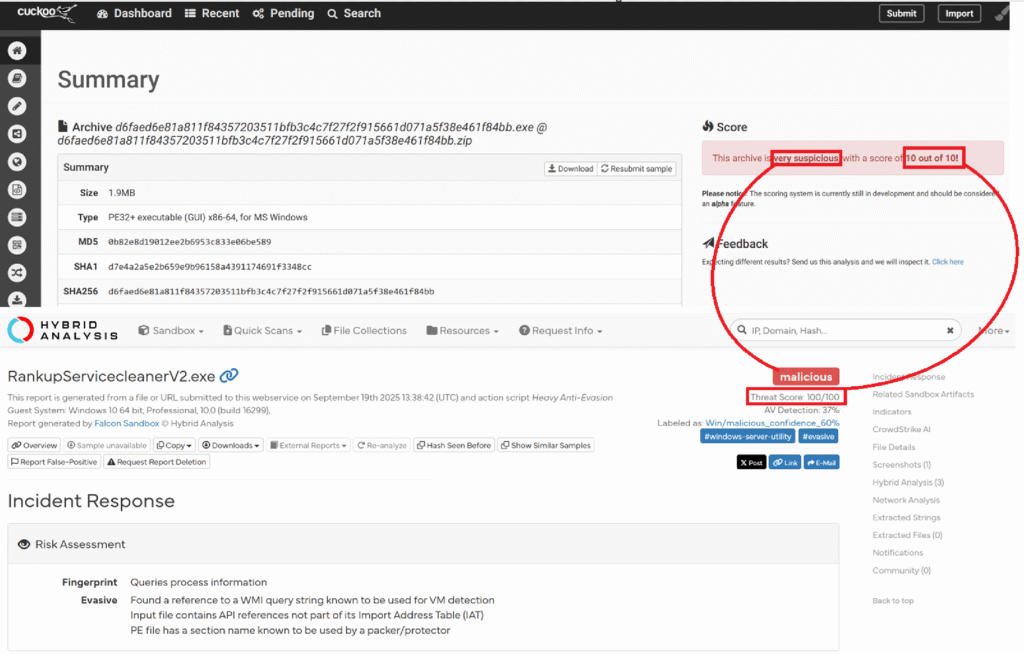
First of all, Cuckoo successfully gives us the summary result that malware is completely harmful.
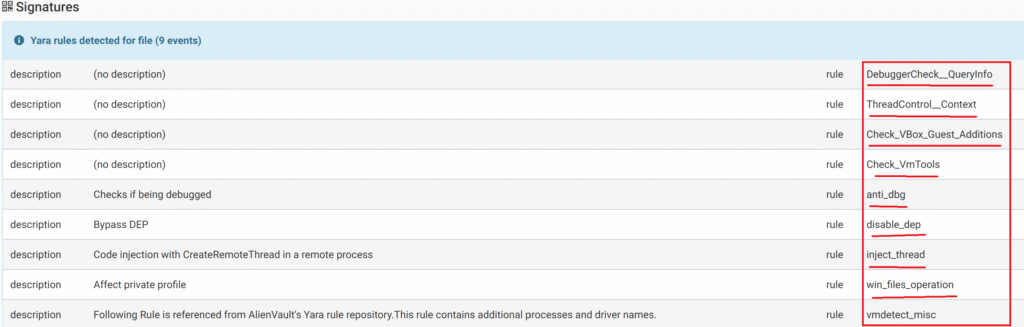
It then provides information about the vulnerability rules the malware has hit. Some of these include:
DebuggerCheck__QueryInfo: This rule attempts to determine whether the malware itself is running in a debugger environment. This can help it determine whether it’s being analyzed by an analyst, which will allow it to avoid this. Alternatively, it can reveal its reverse engineering logic and intent.
anti_dbg: This rule detects debuggers and forces them to be disabled.
Check_VBox_Guest_Additions: This rule allows the malware to determine whether a dynamic analysis is being performed and can act harmless.
Check_VmTools: This is similar to the explanation above.
disable_dep: DEP is a security feature built into Windows. Its primary purpose is to ensure that only code regions in memory are executed and to prevent data areas from being executed. This makes memory-based exploits (such as buffer overflows and rips) more difficult to execute.
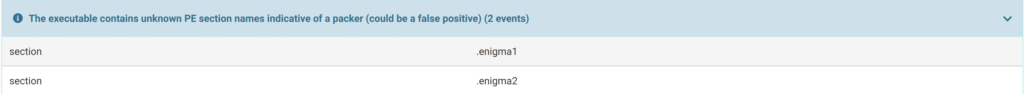
When we look at the results of the Section section, we see it as enigma, which may mean that it is actually packaged.
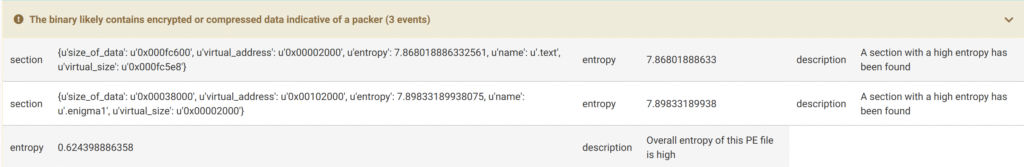
The irregularity value in the sections also appears to be very high. This could mean that it’s packed. As Enigma suggests, it could have been packed, and in this case, the code might have been packed and unpacked at runtime to avoid static analysis.
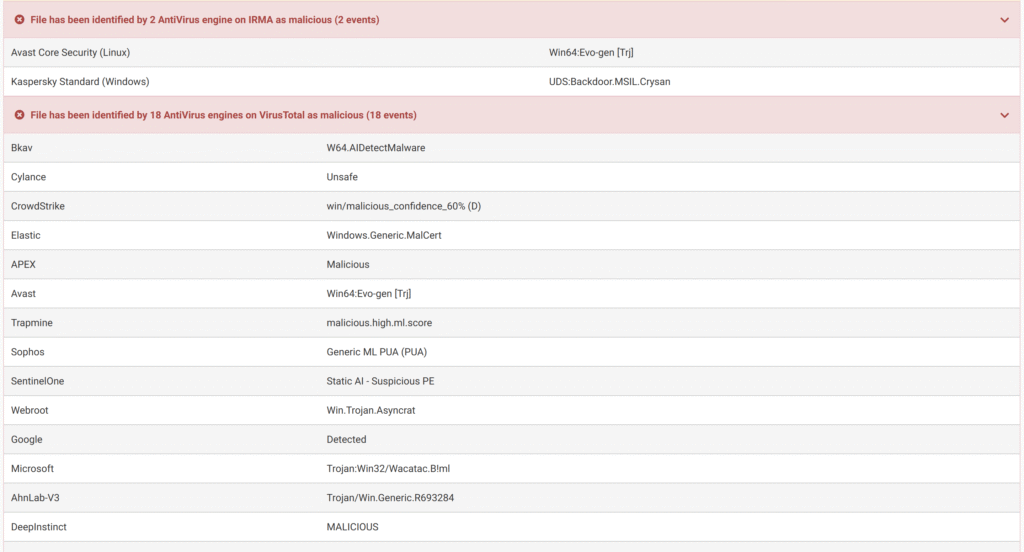
Finally, it informs us that it has been labeled as malicious by many vendors.
Now let’s look at the Hybrid-Analysis side.
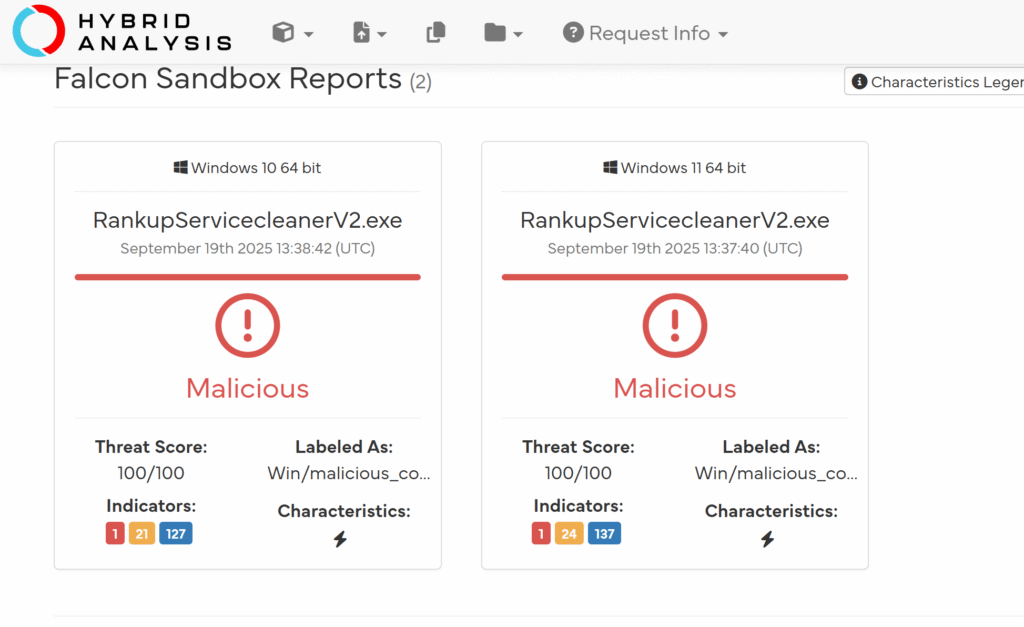
Hybrid-analysis relies heavily on Crowdstrike Faclon’s sandbox capability. When we look at it, it has been tested as 100/100 malicious, just like the cuckoo.
Now let’s look at the findings in order.
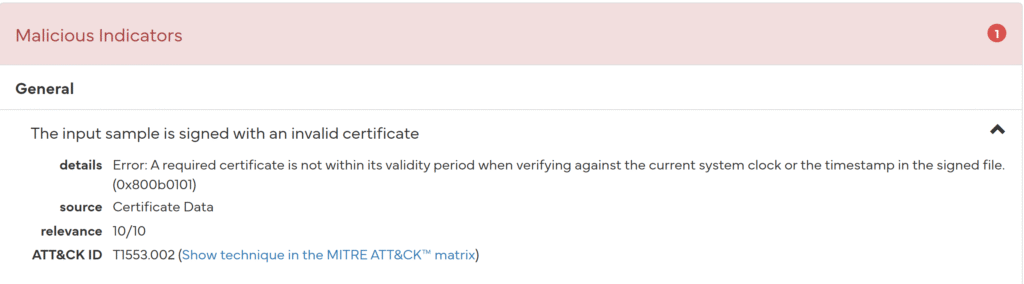
The first and most critical one is the expiration of the certificate.
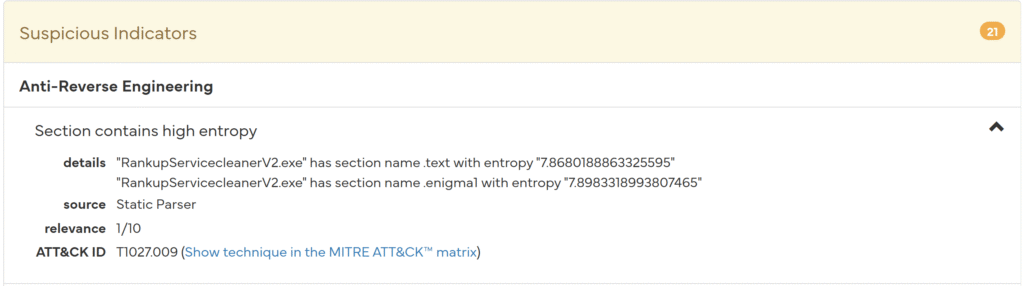
What follows is the finding that the entropy value is very high, just like the cuckoo.
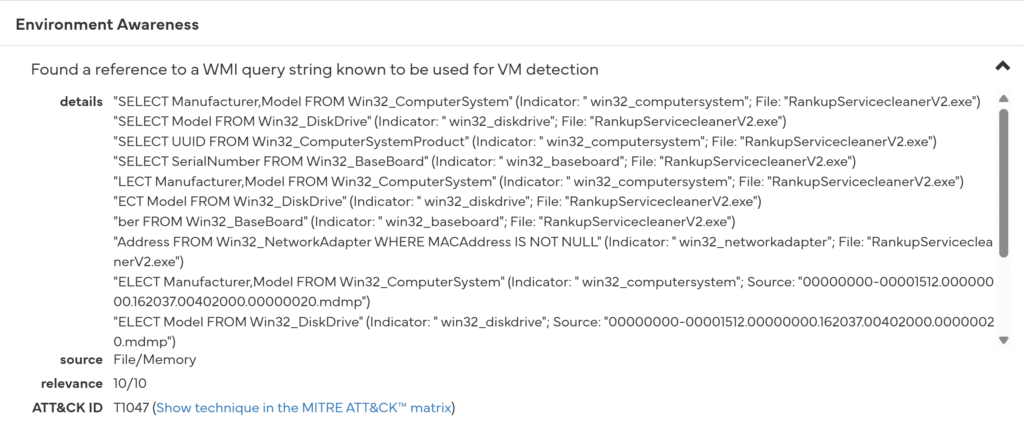
| Query | Goal |
|---|---|
SELECT Manufacturer, Model FROM Win32_ComputerSystem | Hardware model |
SELECT Model FROM Win32_DiskDrive | Disk model |
SELECT UUID FROM Win32_ComputerSystemProduct | UUID Learn |
SELECT SerialNumber FROM Win32_BaseBoard | Anakart seri numarası |
SELECT MACAddress FROM Win32_NetworkAdapter WHERE MACAddress IS NOT NULL | Mac Address |
When you look at it, under the “Environment Awareness” category, malware may actually be trying to understand whether it is running in a virtual or physical environment.
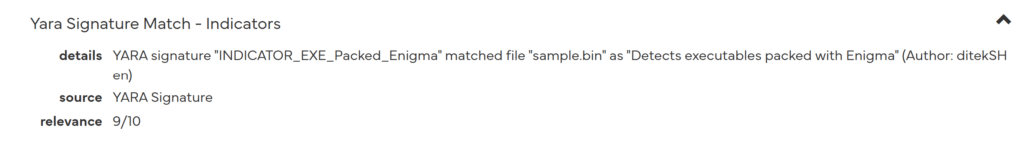
Yara rule matched. The sample.bin file appears to have been encrypted/packaged with Enigma. This may be done for a variety of reasons, including hiding the content and making reverse engineering more difficult.
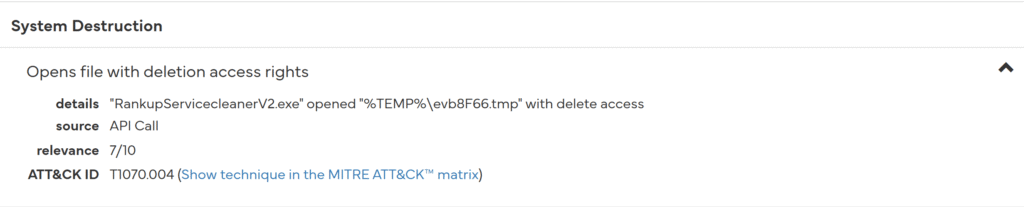
It appears that it opens the file on Temp with delete rights, which is a method that can be used to eliminate traces.
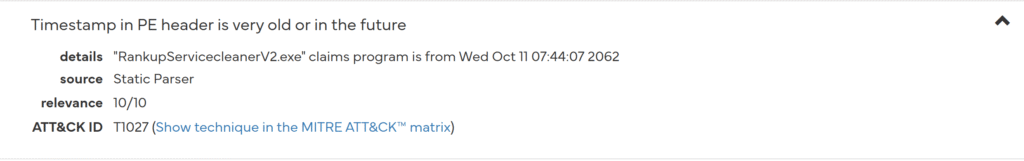
The timestamp date which located in PE header is show very future. It is suspicious.
And then it shows many informative links, but not all of them may be directly related to the maliciousness of the file.
In conclusion, we can say that both sandbox sites produce highly accurate detections. However, for analysts who want to spend more time delving into the details and trying to understand the malware’s deeper objectives, hybrid analysis is more effective.
Likewise, cuckoo may be more satisfactory for analysts who want a more summary and consolidated result.
If you ask my opinion, if I want to subject a malware to dynamic analysis, my choice would be hybrid analysis.
Leave a Reply