
I am planning to install Sysmon on the Ubuntu distribution. If you are going to do this on a different Linux distribution, you can follow the steps in the link below.
https://github.com/Sysinternals/SysmonForLinux/blob/main/INSTALL.md
So, let’s start to install Sysmon
1.
wget -q https://packages.microsoft.com/config/ubuntu/$(lsb_release -rs)/packages-microsoft-prod.deb -O packages-microsoft-prod.deb2.
sudo dpkg -i packages-microsoft-prod.deb3.
sudo apt-get update4.
sudo apt-get install sysmonforlinuxIf you receive the following error at this stage, try the next step.
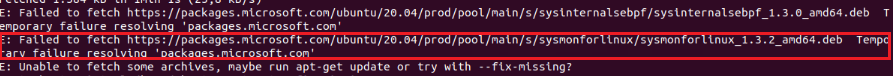
5. Note: Only try this step if you get an error in step 4.
sudo apt-get install sysmonforlinux --fix-broken
At this point, Sysmon has been installed, but sysmon also works with a config file. The relevant config file also indicates which logs sysmon will collect. You can obtain a basic Sysmon Config file from the link below.
https://gist.github.com/olafhartong/56bfbbe1a43ba675fdf5b9f194d608af
Then we can import our config file with the relevant command.
sysmon -accepteula -i sysmon-linux-sample-config.xml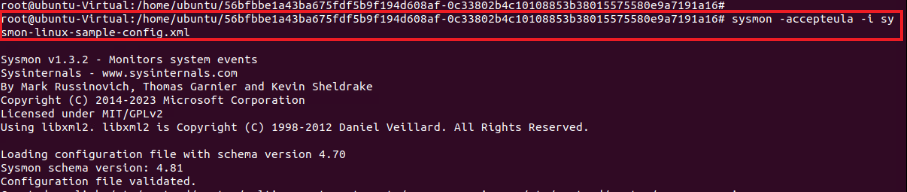
After this stage, Sysmon starts writing its logs to its own log file. We can use the following command to see the logs it writes in real time.
tail -f /var/log/syslog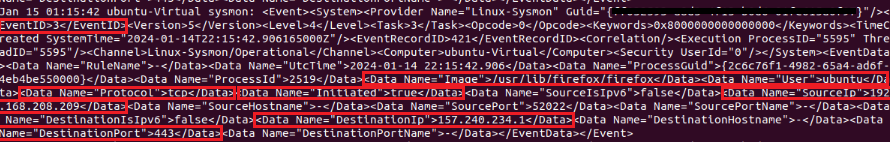
If we need to examine an example log, as we see, the Event ID appears to be 3. If Event ID is 3, it means that a TCP connection has been started. Besides, specifically for this log;
->Protocol used,
->With which User it was done,
->Whether the connection was established successfully or not,
->Information such as Source IP, Source Port, Dest IP, Dest Port information are provided to us.
In addition, you can access information about what other Event IDs mean in the table below.
| ID | Tag | Event |
|---|---|---|
| 1 | ProcessCreate | Process Create |
| 2 | FileCreateTime | File creation time |
| 3 | NetworkConnect | Network connection detected |
| 4 | n/a | Sysmon service state change (cannot be filtered) |
| 5 | ProcessTerminate | Process terminated |
| 6 | DriverLoad | Driver Loaded |
| 7 | ImageLoad | Image loaded |
| 8 | CreateRemoteThread | CreateRemoteThread detected |
| 9 | RawAccessRead | RawAccessRead detected |
| 10 | ProcessAccess | Process accessed |
| 11 | FileCreate | File created |
| 12 | RegistryEvent | Registry object added or deleted |
| 13 | RegistryEvent | Registry value set |
| 14 | RegistryEvent | Registry object renamed |
| 15 | FileCreateStreamHash | File stream created |
| 16 | n/a | Sysmon configuration change (cannot be filtered) |
| 17 | PipeEvent | Named pipe created |
| 18 | PipeEvent | Named pipe connected |
| 19 | WmiEvent | WMI filter |
| 20 | WmiEvent | WMI consumer |
| 21 | WmiEvent | WMI consumer filter |
| 22 | DNSQuery | DNS query |
| 23 | FileDelete | File Delete archived |
| 24 | ClipboardChange | New content in the clipboard |
| 25 | ProcessTampering | Process image change |
| 26 | FileDeleteDetected | File Delete logged |
| 27 | FileBlockExecutable | File Block Executable |
| 28 | FileBlockShredding | File Block Shredding |
| 29 | FileExecutableDetected | File Executable Detected |
Now, let’s observe what kind of activities a malicious file performs on Linux with Sysmon.
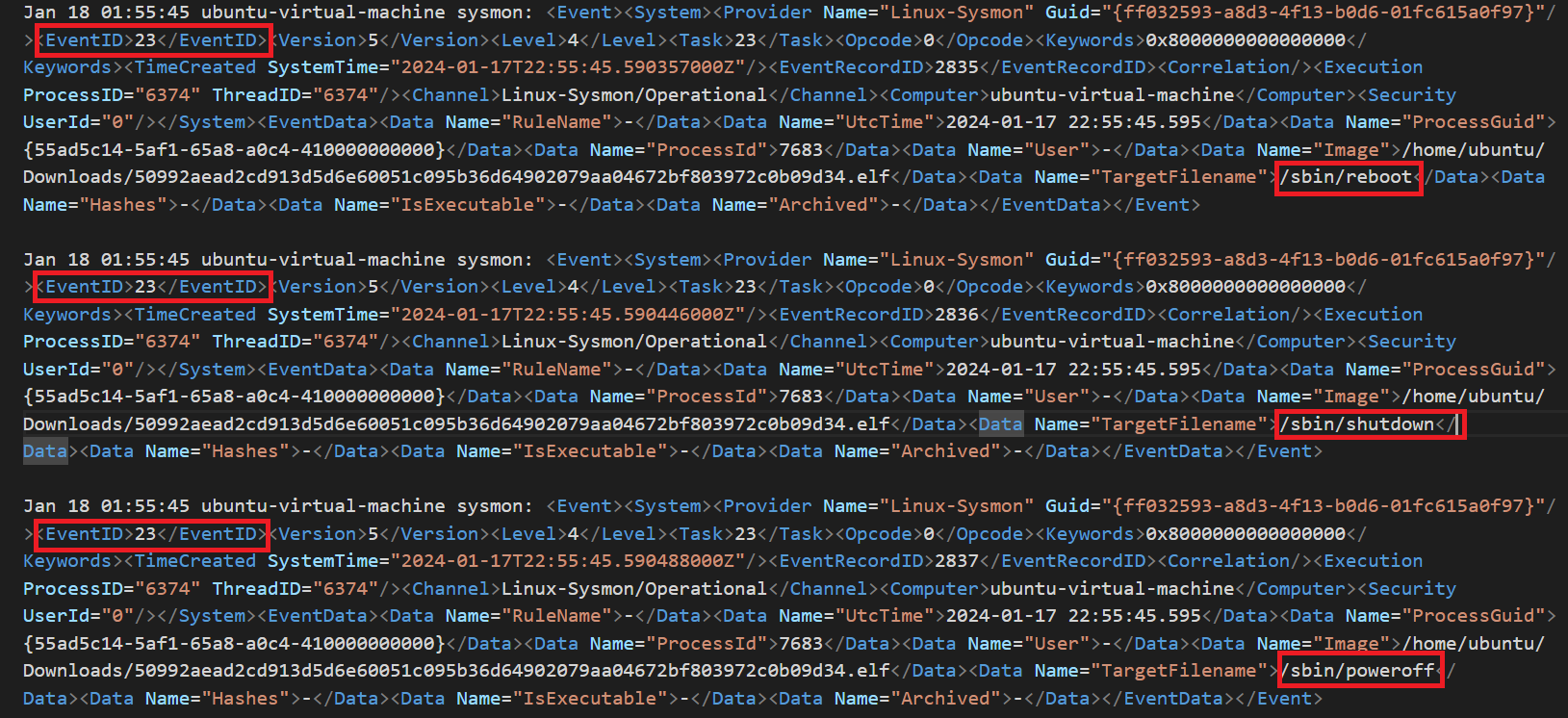
When we look at the logs, we see some events with ID 23. As we can confirm from the table above, event ID number 23 means file deletion. When we look at some of the deleted files, they are binary files such as reboot, shutdown, halt, poweroff. The reason why the malware deletes these may be to increase its control over the endpoint and prevent the endpoint from being closed or restarted.
When we continue to examine the logs, we see that many 3 ID events occur.
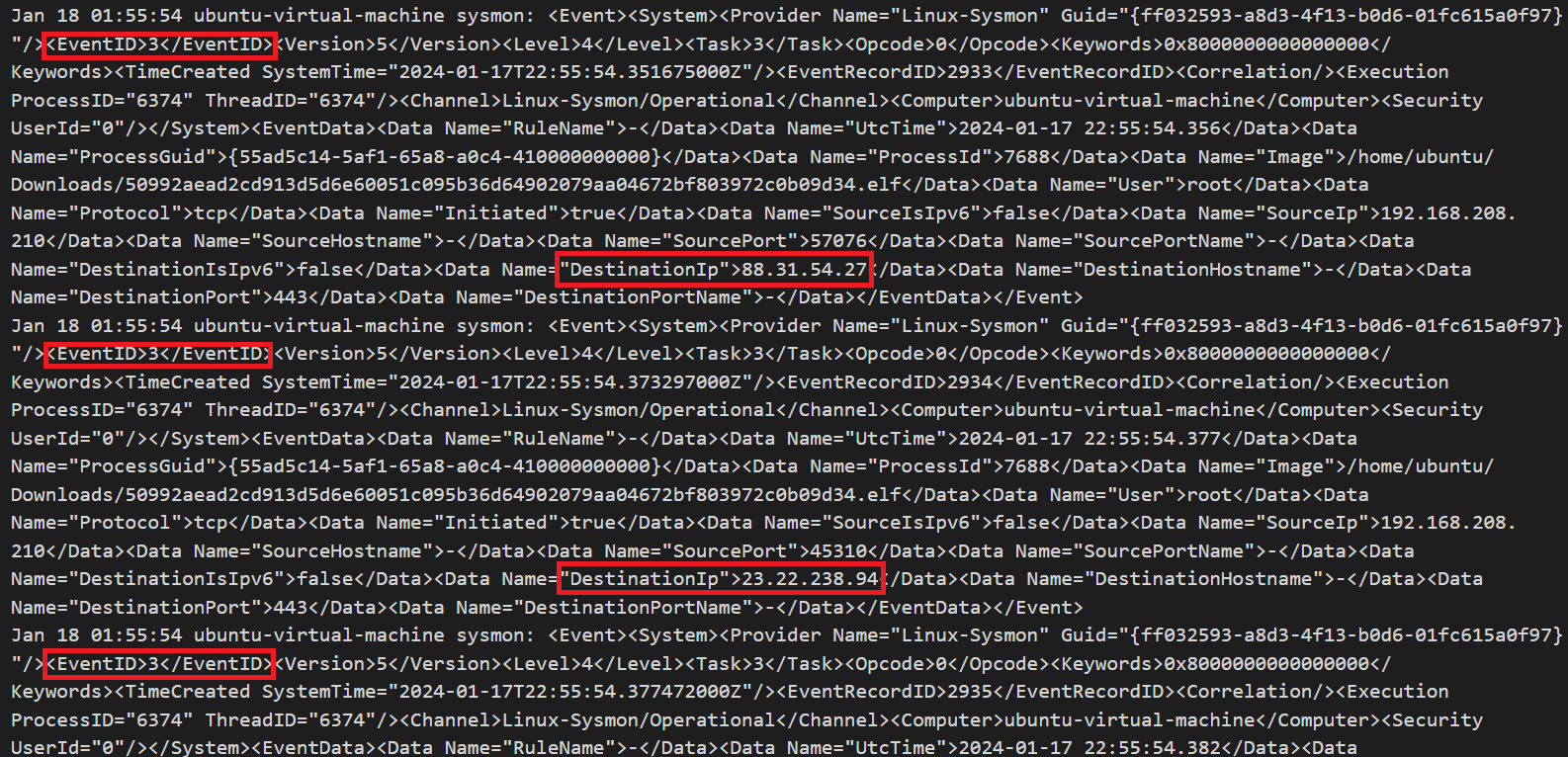
It is observed that SYN packets, which are the first packets of TCP connections, are sent to different IPs.
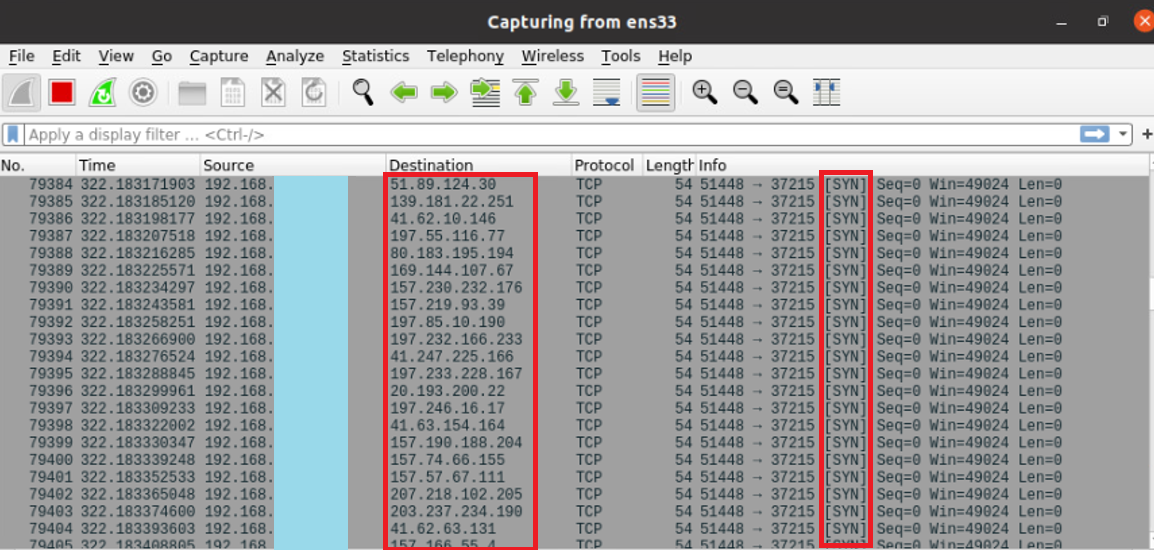
In other words, this malware apparently prevents the system administrator or endpoint owner from accessing functions such as rebooting and shutting down the system after a virus infection, and then initiates a TCP handshake to many different IPs, increasing resource consumption to fill the host’s bandwidth and use system memory. may be aiming for. Because the size of a SYN packet in memory is approximately 62 bytes.
As a result, we can examine activities with Sysmon on Linux endpoints, as we can on Windows endpoints, and provide a layer of visibility for malicious activities.
Leave a Reply