
Process explorer is a sysinternals tool, and like every sysinternals tool, it can be used for operations such as system administration and troubleshooting. Process Explorer, which is our subject, can be thought of as an advanced version of Task Manager. Process Explorer, with its features, can provide us with more detailed information and telemetry data about the processes running on our system.
Let’s learn some ways how we can catch malicious software that may exist in our system using Process Explorer.
Let’s download the Process Explorer from https://learn.microsoft.com/en-us/sysinternals/downloads/process-explorer
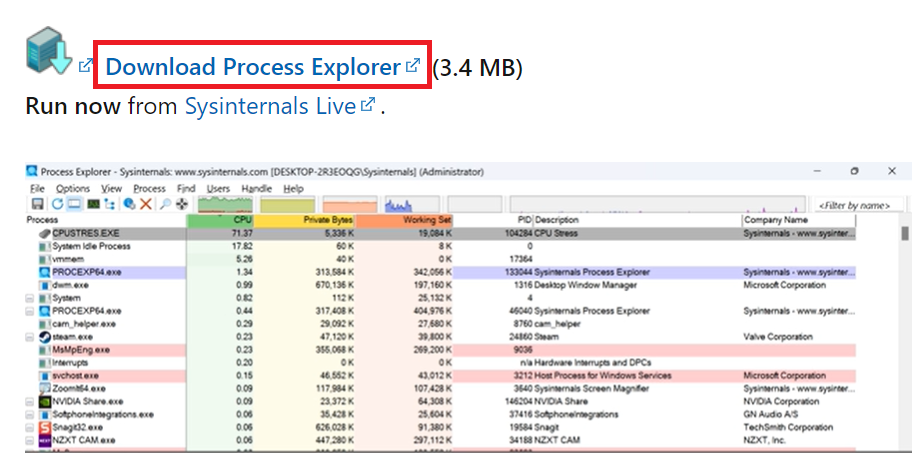
This software does not require any installation and can be run directly. When we run the application, we see all the processes running on our system and their child processes.
Let’s see how to detect malware step by step.
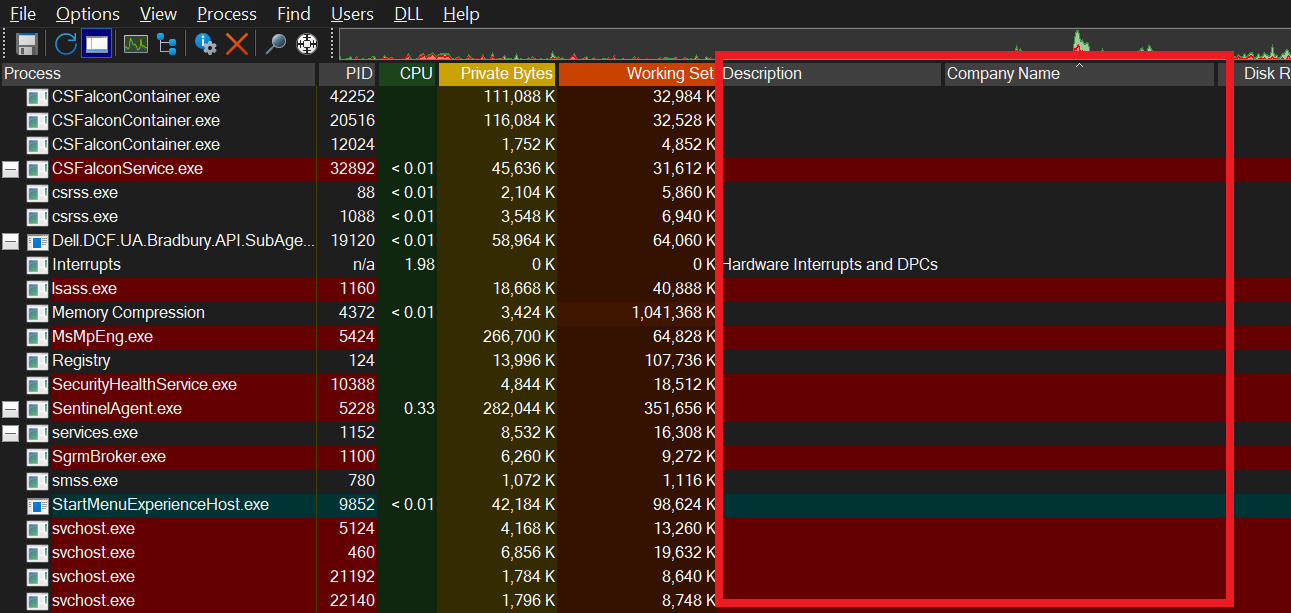
1- CPU, IO, RAM usage
Malware has a tendency to use too much system resources. Because the operations performed by pests require high amounts of system resources.
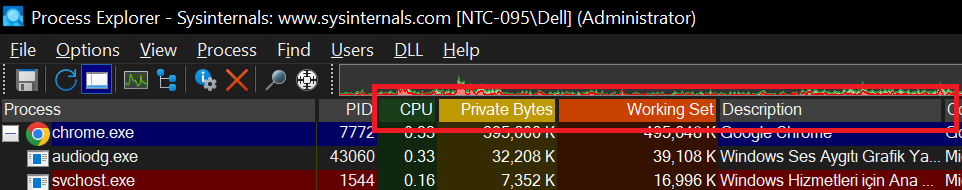
By clicking on the titles in the red square, we can ensure that the processes that consume the system’s resources the most appear at the top.
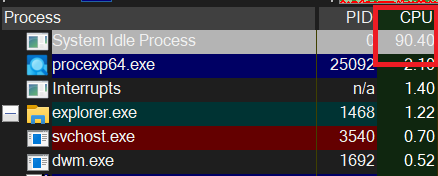
However, it would not be correct to assume that every process that uses high system resources is malware. For example, when we sort by CPU, it appears that the “System Idle Process” process occupies around 90% of the processor. However, this process is a Microsoft process and this actually means that our processor is around 10% busy.
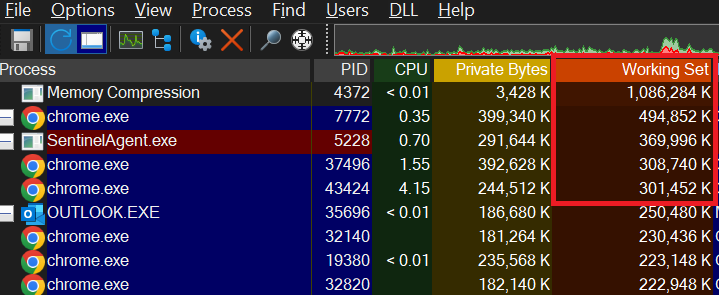
Or when I sort by RAM usage, the “Memory Compression” process appears at the top. This is actually a process that belongs to Windows and is a system that aims to save space by using RAM more effectively. In other words, we can say that it aims to represent the same data using fewer bits.
2- Description and Company Name
Metadata of malware may not include information such as “Company Name” and “Description“. The absence of such information in processes may mean that that process may be malicious software.
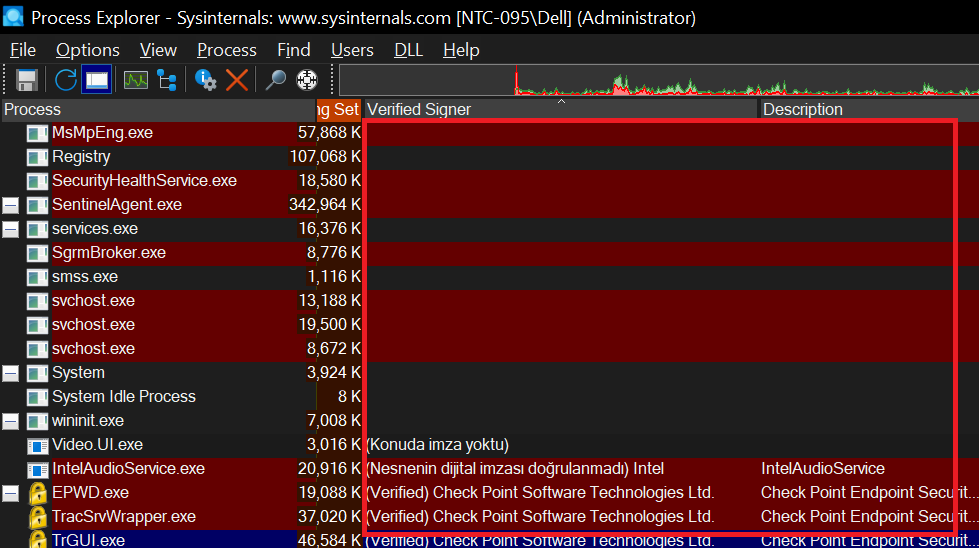
3- Verified Signer
Process Explorer also gives us information about whether the processes are signed or not, and it is not expected to be the signature of a malicious software. There may be times when it does, but if there is no signature, we should increase our suspicions about the relevant process.
4- Virus Total Hash Check
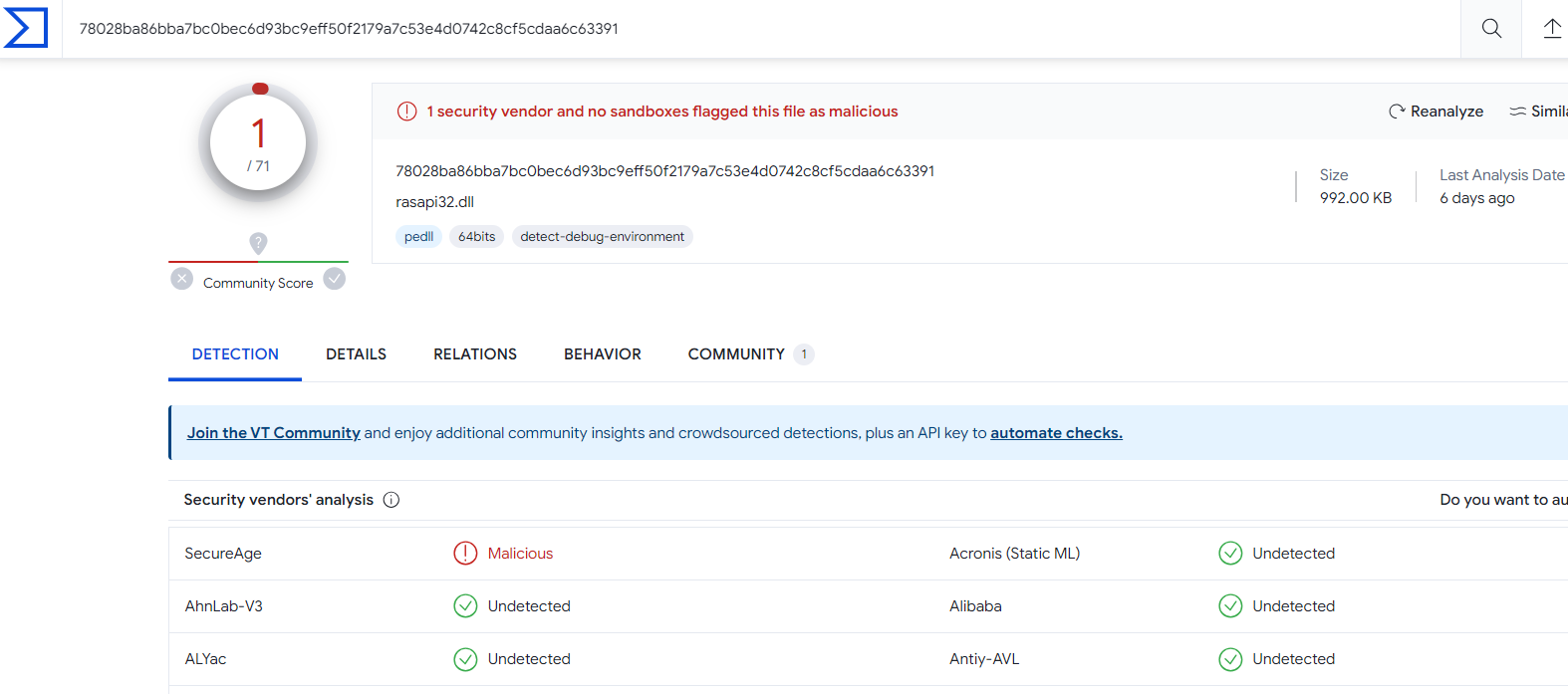
We can obtain information about the processes and the .DLL files loaded into those processes whether they are marked as malicious by more than 70 Antivirus vendors in Virus Total.
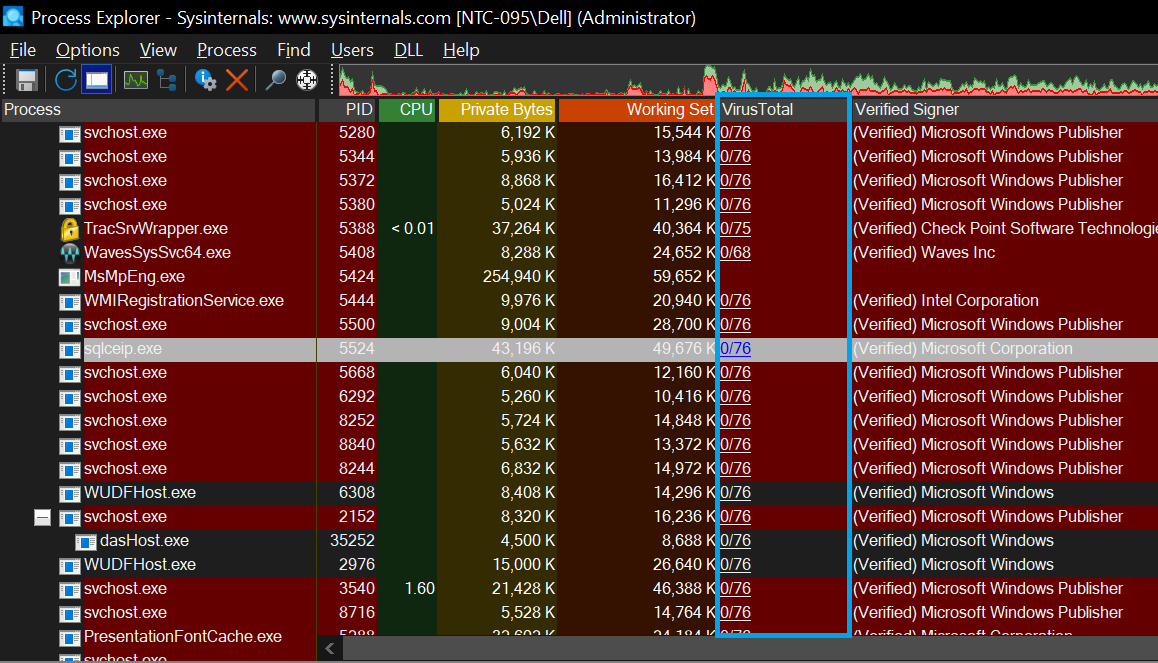
As you can see, the process named “sqlceip.exe” seems clean for 76 vendors, but when we look at the .dll files that loaded this process, the “rasapi32.dll” file was recognized as malicious by a vendor.

When we click on the red text “1/76”, it directs us to Virus Total’s website. Thus, we can also see the information about which manufacturer defined the relevant .dll file as malicious.
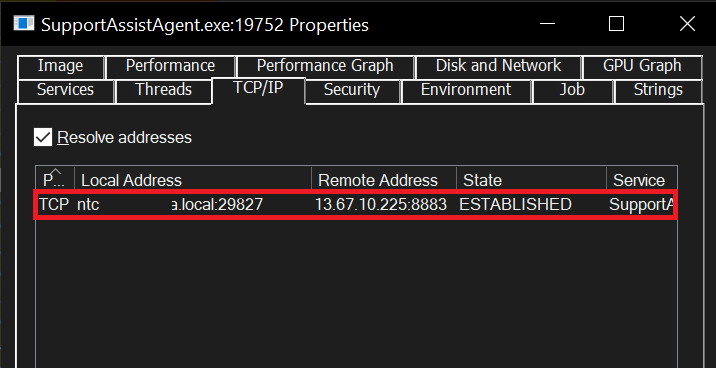
5- TCP/IP Connections
Malicious processes can communicate with Command and Control centers to download larger payloads or simply receive commands. Therefore, we can go to the TCP/IP tab in the Properties of a Process and see which destination and port the process has initiated a connection to. If you suspect that a process is a malicious process and you see that it is initiating a connection to a destination, it would be a good idea to try to get more information about this destination IP.
6- Strings
The Strings Tab brings us the strings in a process’s memory in a format that we can read.
Malicious patterns can be searched among these strings, or if we are sure that a process is malicious, these strings can be useful for the IOCs.

Then let’s run our tests with a real malicious file.
Note: Only run files that you are sure are malicious in an isolated environment.
I obtained a real malicious file and when I run it on the endpoint, it is observed that it consumes about 70% of the CPU, albeit for a short time. We also observe that the process kills itself quickly.

In the Signature section contains “No Signiture Present in the Subject”. In other words, there are suspicious situation that I mentioned in parts 3 above.

When we continue the checks, we see that this process is marked as malicious in 36 of 76 vendors on Virus Total. The injected .dll files at the bottom look clean because these .dlls are, on a large scale, Microsoft’s own and legal .dll files.

Thus, by using Process Explorer, we can obtain information about whether the processes running on our system are malicious or not.
When we go to the properties of the process and go to the TCP/IP section, we can see the IPs to which the process has established connections.

When we check, we see that one of the IPs is an IP address labeled as malicious.

Leave a Reply