CVE-2023-48795 is a vulnerability in the SSH transport protocol with certain OpenSSH extensions in OpenSSH versions prior to version 9.6 and some other products. This vulnerability could allow remote attackers to bypass integrity checks by bypassing some packets, resulting in a connection between a client and server where some security features are downgraded or disabled. CVE-2023-48795, NVD release date is 12/18/2023. The criticality level is 5.9.
We can use the scanner at https://github.com/RUB-NDS/Terrapin-Scanner as a way to find out whether this vulnerability affects our SSH servers.
You can install by following the instructions on Readme.md, or you can also use the compiled binaries from the address below.
https://github.com/RUB-NDS/Terrapin-Scanner/releases/tag/v1.1.0

It is very easy to use.
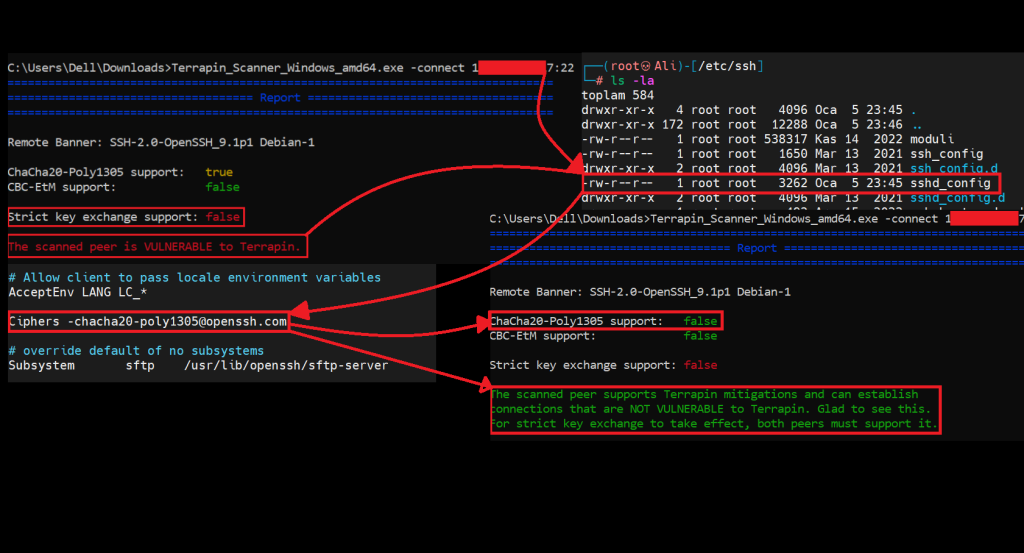
Terrapin_Scanner_Windows_amd64.exe -connect <IP>:<Port>As a result of a request I make to a server with a vulnerable SSH connection, the scanner tells us that this connection does not support Strict Key Exchange.

As a result of my request to a server with a vulnerable SSH connection, the scanner tells us that this connection supports Strict Key Exchange and does not contain this vulnerability.

Mitigation
Strict key exchange should be made mandatory or support for vulnerable algorithms should be removed. Strict key exchange is a retroactive modification that introduces sequence number resets to the SSH handshake, eliminating the attacker’s ability to inject packets during the initial unencrypted handshake.
Now, let’s perform mitigation for OpenSSH step by step. To do this, go to /etc/ssh and find the sshd_config file and go into it with nano or cat.
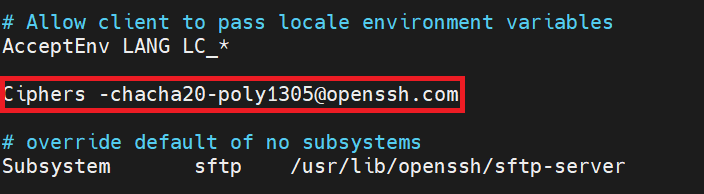
Then paste the relevant line into it. This line will disable the vulnerable algorithm chacha20-poly1305.
Ciphers -chacha20-poly1305@openssh.com
When I perform the above steps on my vulnerable SSH server, it is seen that the relevant server is no longer affected by this vulnerability after being checked with a scanner.

Resources
https://nvd.nist.gov/vuln/detail/CVE-2023-48795 https://threatprotect.qualys.com/2023/12/22/ssh-vulnerability-used-in-terrapin-attacks-cve-2023-48795/ https://jfrog.com/blog/ssh-protocol-flaw-terrapin-attack-cve-2023-48795-all-you-need-to-know/ https://www.tenable.com/plugins/nessus/187315
Leave a Reply