RDP caches left at endpoints aren’t just a performance optimization; they can also become dangerous monitoring points. When RDP sessions are decoded with BMC tools and frames are reassembled using tools like RDP cache stitcher, attackers can observe session content and user behavior. This can provide a platform for persistent access and lateral movement that bypasses detection mechanisms. In the article below, I demonstrate how malicious actors can exploit this critical situation by showing a demo environment and explaining what can be done to prevent it.
The path where these bitmap cache binary files are kept is below.
C:\Users\%USERNAME%\AppData\Local\Microsoft\Terminal Server Client\Cache
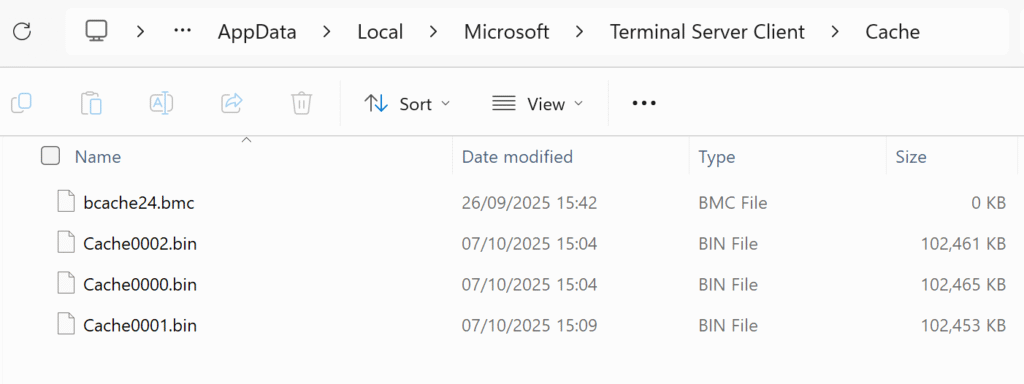
These bitmap cache files are in binary format and the images cannot be accessed unless we decode them, and we can decode them with the bmc tool. You can access the tool from the github link below and you can clone it.
https://github.com/ANSSI-FR/bmc-tools
git clone https://github.com/ANSSI-FR/bmc-tools.gitHowever, if you do this with a Linux distro via WSL it will be easier to use.
Now, this tool is for decoding to binary. We also need a tool that simplifies the process of combining decoded image frames. This is the RDP cache stitcher tool. You can also find it at the link below.
https://github.com/BSI-Bund/RdpCacheStitcher/releases/tag/v1.1
Now let’s decode the binary using bmc tools via WSL. You can decode it by specifying the source and output locations and providing the necessary parameters with the command below.
python3 bmc-tools.py \
-s "/mnt/c/Users/$USER/AppData/Local/Microsoft/Terminal Server Client/Cache/Cache0001.bin" \
-d "/mnt/c/Users/$USER/Downloads/bmcoutput/"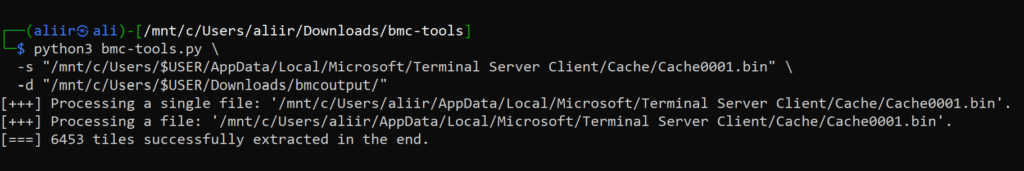
When we go to the output path, we can see that the image frames have been decoded. However, since these are small image fragments, it can be difficult to associate them at first glance.
So let’s open the RDP cache stitcher application, click new case and select the relevant output folder.
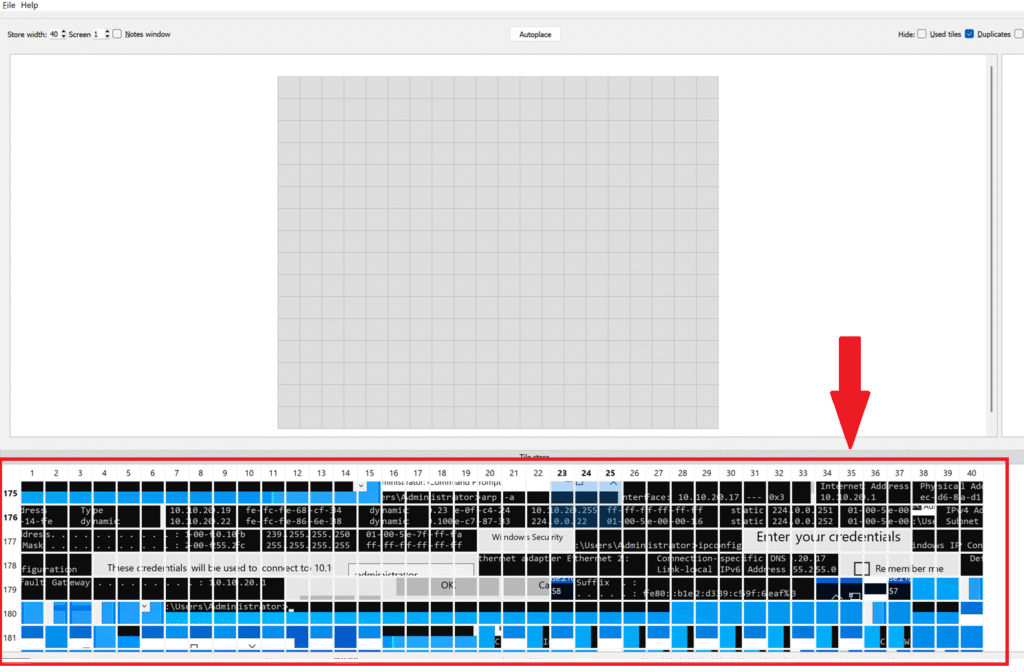
We can see the image frames. We can combine them in the empty space above.
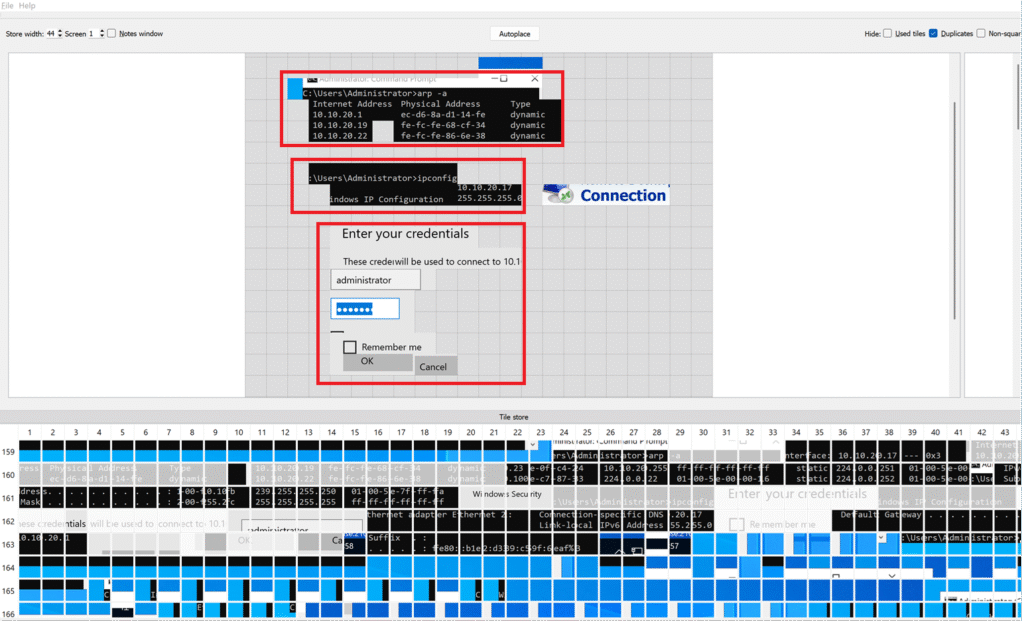
Although it may take some time, critical information can be gathered.
Mitigation
1- One of the steps that can be taken to mitigate this attack vector is to clear the cache by running the following bash after each rdp session.
$paths = @(
"$env:LOCALAPPDATA\Microsoft\Terminal Server Client\Cache",
"$env:LOCALAPPDATA\Microsoft\Terminal Server Client\StaticCache",
"$env:LOCALAPPDATA\Microsoft\Terminal Server Client\Servers"
)
foreach($p in $paths){
if(Test-Path $p){
Remove-Item -Path "$p\*" -Recurse -Force -ErrorAction SilentlyContinue
}
}2- Monitoring the path below with Sysmon can also enable us to be aware of the activities on this path.
C:\Users*\AppData\Local\Microsoft\Terminal Server Client\Cache*
Leave a Reply